IDP Integration Configuration
Integration with Identity Provider (IDP) - MC Connect
We use auth-broker microservices to integrate with MC Connect. The goal of the service is to provide a way for the client to authenticate via MC Connect. Auth-broker uses SAML to talk to MC Connect and OAuth2 to communicate with the client (UI).
SAML Configuration
SAML configuration including the signing and encryption certificates is contained in saml-metadata.xml. The file is provide by the MC Connect team and it is stored in an S3 bucket. Build process copies the file to the container, so auth-broker can use it to communicate with MC Connect.
MCCUP Configuration
SAML response from MC Connect doesn't contain information about user roles. Auth-broker calls MCCUP to retrieve the roles. MCCUP uses mutual TLS for authentication; the key and the certificate for the integration are stored in the same S3 bucket as saml-metadata.xml. Build process copies the files to the container which generates a Java Key Store used by auth-broker when communicating with MC Cup.
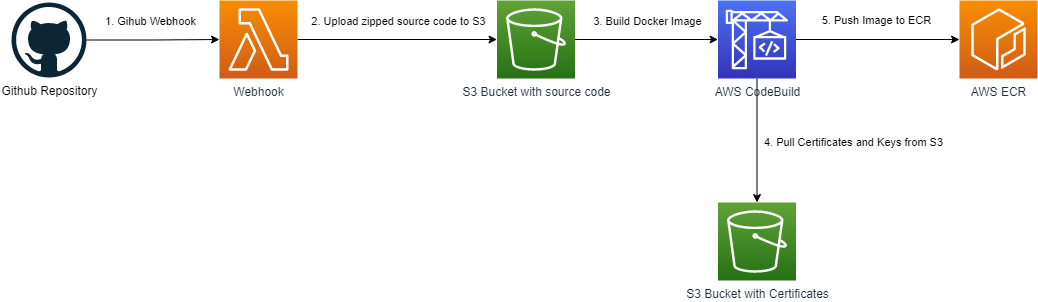
Build Pipeline
It's Ops team's responsibility to upload saml-metadata.xml, key, and certificate files to the S3 bucket that's used by the build process to embed the files in the Docker image. The development team doesn't have access to these files.